- Home Server with Raspberry Pi & FreeBSD
- Home NAS Using a Raspberry Pi
- Bastille Jail Management on Raspberry Pi
- Pi-Hole with FreeBSD using AdGuard Home
I originally purchased my Raspberry Pi to run Pi-Hole, which functions as a whole-house ad-blocker. Technically, Pi-Hole is just a script that installs and configures dnsmasq and loads a bunch of domains to block at the DNS level. When a website tries to load something from, say, ads.google.com, normally your computer will connect to a DNS server that translates the web url to an IP address. Your browser goes to the IP address and then asks for the content. Sometimes, it’s an unwanted ad.
Usually, your DNS server is provided by your ISP and you’re not even aware of it. A Pi-Hole is a local DNS server that you use instead. First you computer will check to see if the Pi-Hole resolves (points to the IP address) a domain. If the Pi-Hole blocks it, it won’t load. Your computer will never communicate with the servers that provide ads. If the Pi-Hole doesn’t block it, it will query a public DNS server to look up the domain for you (Cloudflare, Google, etc.). Pi-Hole works as a caching DNS server, too, since that’s what dnsmasq is usually used for. This means that it saves the DNS entries after you have visited a site so it doesn’t have to make that extra step later. The advantage of a caching DNS server is that it speeds up your browsing by eliminating that last step.
Unfortunately, Pi-Hole isn’t available for FreeBSD. Now that I’ve switched my Pi over to FreeBSD I’ll have to come up with a new solution. That shouldn’t be too hard because Pi-Hole is just dnsmasq with a big list of domains pointed to localhost, but the big advantage of Pi-Hole is the convenience. The script does all the configuration for you and receives updates. Let’s see if we can make this work without Linux.
In a previous article, I installed Bastille to manage jails. Bastille comes with some nifty templates, and in this guide I’ll use a template for AdGuard Home to set up a whole-home adblocker.
Create a Pi-Hole using FreeBSD and AdGuard Home
- Bootstrap Bastille Tempalte
Use the following command to download and bootstrap the AdGuard Home template.bastille bootstrap https://gitlab.com/bastillebsd-templates/adguardhome - Create Jail Using Bastille
The following command tells Bastille to create a jail named adguardhome using FreeBSD 13.1 at the IP address 10.4.4.4 on the loopback network bastille0. See my article on installing Bastille if you would like more detailed explanations for any of these things. The jail name and IP address can be whatever you want, just so long as the jail IP is a reserved local IP address that isn’t already in use.bastille create adguardhome 13.1-RELEASE 10.4.4.4 bastille0 - Apply Template to Jail
Now we apply the template we downloaded in step 1 to the jail we created in step 2:bastille template adguardhome bastillebsd-templates/adguardhome - Login
You can now login to AdGuard Home by pointing a web browser to the local IP address of your Raspberry Pi. By default, the username should be adguard and the password BastilleBSD!. To get your Pi’s local IP address, type ifconfig: Note that this is the IP of the Pi, not your jail.root@beastie:/etc # ifconfig genet0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=68000b<RXCSUM,TXCSUM,VLAN_MTU,LINKSTATE,RXCSUM_IPV6,TXCSUM_IPV6>
ether dc:a8:32:c8:28:4d
inet 192.168.1.2 netmask 0xffffff00 broadcast 192.168.1.255
media: Ethernet autoselect (100baseTX <full-duplex>)
status: active
nd6 options=29<PERFORMNUD,IFDISABLED,AUTO_LINKLOCAL>
The default password did not work for me. If you log into your jail using $ Bastille console adguardhome you can change it by editing /usr/local/bin/adguardhome/AdGuardHome.yaml. You cannot enter a plain text password here. Instead, you’ll need to include a hash. You can generate one here. The hash begins with $2y$ and you need to select Bcrypt (Apache v2.4 onwards). If you don’t trust some random website (really, it shouldn’t be a problem), then you can install Apache and use the htpasswd command.
When you login you should see a page like this: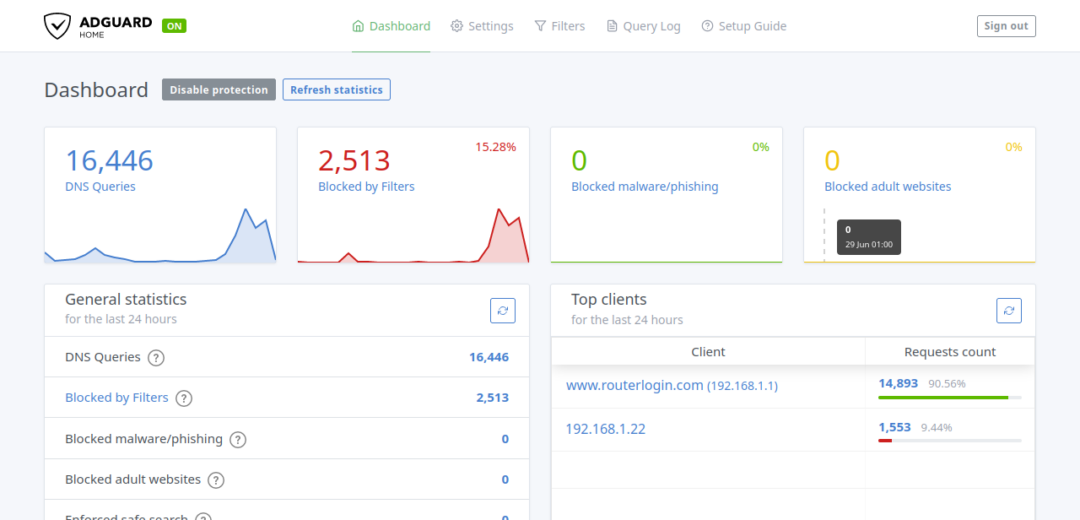
- Set up Devices/Router
You can set up devices individually. How to do this will vary depending on the device, operating system, etc. but it will always involve changing the device’s DNS servers to the IP address of your Pi (remember, the Pi itself, not the jail IP). Most home networks have many devices and some won’t even give you the option of configuring DNS settings. It’s much easier to configure your router to use the Pi as a DNS server and this will direct all the traffic on your home network through it.
There are many different router manufacturers so this guide will just cover mine, but the process is pretty much the same for all of them. Also, mine is currently a Netgear, which is one of the most common routers on the market.
First, log in to your router. If you have a Netgear you can type https://www.routerlogin.net to your browser window and it will take you there. You can also just type in the IP address, which is usually 192.168.0.1 or 192.168.1.1. If none of these work you may have to consult the user guide for your router.
You’ll have to sign in. The username and password are usually the same as your username/password to connect to wifi or admin and the wifi password.
Again, consult your manual if this is not the case. Find the DNS settings (in my case, “Internet setup”) and put your Pi IP address as the primary DNS server and 1.1.1.1 as the secondary.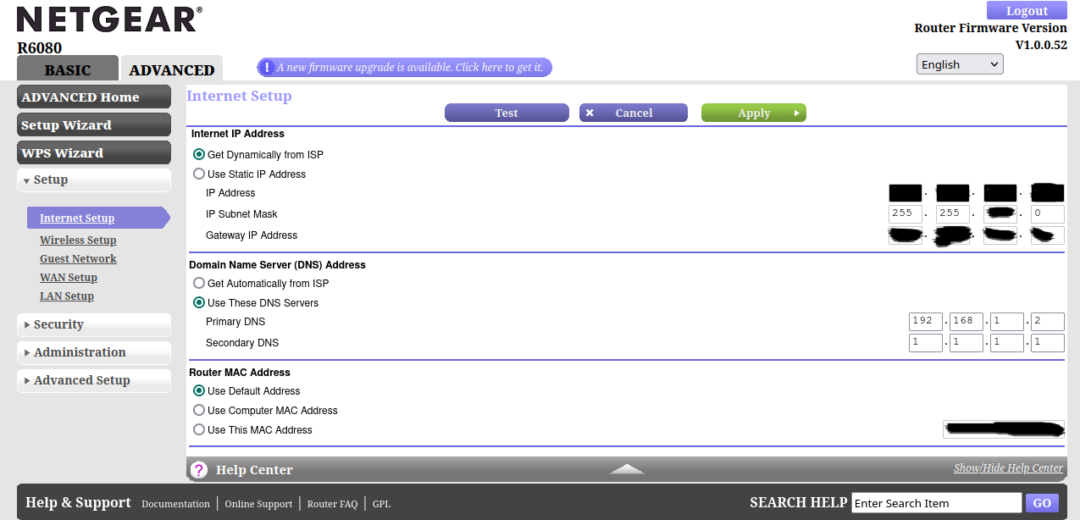
You’ll want a secondary DNS server in case something happens to your Pi or the public DNS server it relies on. I use Cloudflare (1.1.1.1) because they are reliable and more trustworthy than Google. I like Quad9, but that’s what the Pi is using so it wouldn’t make sense as a backup.
Conclusion
Browse the internet a bit and then check to see that everything is running smoothly in the AdGuard Home console. If you see a bunch of DNS queries and some blocks, then things are working as they should. In the future, I’m going to try unbound-adblock, and see how that compares.
If you have any questions, comments, or corrections, you can reach me at [email protected].